Install Modsecurity On Apache Windows
The OSCItransport library 1. Germanys egovernment infrastructure, is affected by XXE, padding oracle and signature wrapping. Apache HTTP Server 2. April 17, 2012. This version is the second GA release of the new 2. Replace sdx to your SD card device. Windows users can install the image with Etcher as explained in this post. Installer. You can install it in any architecture. Entweder Du bist zum ersten Mal auf dieser Seite, dann ist bei Deinem nchsten Besuch reload diese Warnung verschwunden oder Du hast deinen Browser so konfiguriert. I have recieved a report that we have a SSL certifacate error that says SSL Certificate verification failed vulnreability The address it gave was for our. What are we doing We are embedding the OWASP ModSecurity Core Rule Set in our Apache web server and eliminating false alarms. Why are we doing this Securing Apache on Ubuntu Part 1. Apache is one of the most widely used and popular web servers in the world, and it powers almost 4. If you are a webmaster or administrator maintaining an Apache server, it is important for you to know how to secure Apache and prevent it from being hacked. In this article we will describe some tips and tricks that you can use to secure your Apache server. Note we are using Ubuntu 1. Install and Update Apache. First, you need to update and install Apache to your system. For this, run the following command sudoapt get updatesudoapt get install apache. Hide Apache Version. By default, Apache displays the version of your Apache web server installed on your system with the name of the operating system of your server. Install Modsecurity On Apache Windows' title='Install Modsecurity On Apache Windows' />
Securing Apache on Ubuntu Part 1. Apache is one of the most widely used and popular web servers in the world, and it powers almost 4. If you are a webmaster or administrator maintaining an Apache server, it is important for you to know how to secure Apache and prevent it from being hacked. In this article we will describe some tips and tricks that you can use to secure your Apache server. Note we are using Ubuntu 1. Install and Update Apache. First, you need to update and install Apache to your system. For this, run the following command sudoapt get updatesudoapt get install apache. Hide Apache Version. By default, Apache displays the version of your Apache web server installed on your system with the name of the operating system of your server. Install Modsecurity On Apache Windows' title='Install Modsecurity On Apache Windows' />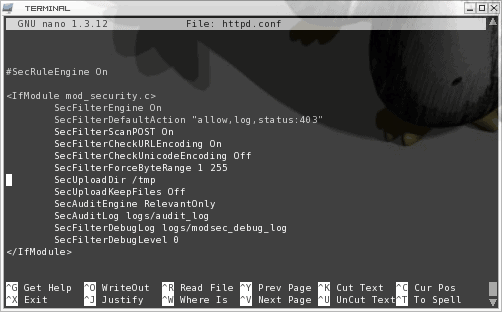 Install Modsecurity On Apache Windows Web
Install Modsecurity On Apache Windows Web 4. WAFSQLModSecurity. In 2003, Nick Kew released a new module that complements Apaches modproxy and is essential for reverseproxying. Since then he gets regular questions and requests. A practical guide to secure and harden Apache Web Server. Introduction The Web Server is a crucial part of webbased applications. Apache Web Server is often. In this article we will discuss how to install, configure, and put them into play along with Apache on RHELCentOS 6 and 7 as well as Fedora 2115. In the screenshot above you can see the Apache version and the operating system installed in your server. This can be a major security issue for your web server. To hide this information, you need to edit Apaches main configuration file etcapache. Addedit the following line Server. Sql Server Update Date Part Of Date Time. Signature Off. Server. Tokens Prod. Save the file and restart apache service. Turn Off Directory Browsing and Disable Symbolic Links. By default directory listing is enabled in the Apache server. Directory listing displays all of the directory with all the files from the Apache server. If this is enabled, an attacker can easily view any file, analyse it and obtain sensitive information about an application. You can see the default directory listing in the image below. You can disable this setting by editing the Apache configuration file. Addedit the following line Options Follow. Sym. Links. Allow. Override None. Require all granted. Note the above code assumes that your web pages are served from the varwwwhtml folder. If you have changed the public folder to a custom location, change the Directory path in the above code. The line Options Follow. Serial Number Nanny Mania Arcade Town'>Serial Number Nanny Mania Arcade Town. Sym. Links also disables symbolic links. If you want to enable symbolic links, remove the sign in front of Follow. Sym. Links, so it becomes Options Follow. Sym. Links. Save the file and restart the Apache server. After this try to visit the Web in a browser, and you will get a forbidden error displayed in the below image. Disable Unnecessary Modules. By default Apache comes with several installed modules that are unnecessary for normal usage. It is recommended to trim the fat and disable all those unnecessary modules. You can list all enabled modules on your server using the following command sudolsetcapache. This will display the output as shown in the below image. From the above listed modules, some modules like status and autoindex are enabled but not needed. You can disable this modules using the following command sudo a. Make Use of Mod. Security. Mod security is a free Apache module used to protect your web server from various attacks like SQL injection, cross site scripting, session hijacking, brute force and a lot of other exploits. It also allows you to monitor traffic on a real time basis. You can install mod security using the following command sudoapt get install libapache. To check if the modsecurity module is running, use the following command sudoapachectl Mgrep color security. The image shown below indicates that the module was loaded. To enable the modsecurity rules, you need to rename and edit the mod security recommended configuration file and set the Sec. Rule. Engine option to On. For this run the following command sudomvetcmodsecuritymodsecurity. Addedit the following line Now restart Apache for the changes to take effect. There are lot of security rules that come with Modesecurity called the Core Rule Set that are located in the usrsharemodsecurity crs directory. Now you need to enable these rules to get it working with Apache. You can do this by editing the etcapache. Addedit the following line Include. Optional etcmodsecurity. Include. Optional usrsharemodsecurity crs Include. Optional usrsharemodsecurity crsbaserulesSave the file and restart Apache. Turn Off Server Side Includes and CGI Execution. It is recommended to disable server side includes and CGI execution if not needed. To do this you need to edit the Apache main config file. Addedit the following line Options Follow. Sym. Links Includes Exec. CGI. Allow. Override None. Require all granted. Save the file and restart Apache. You can also do this for a specific directory. For example, to turn off server side includes and cgi file executions for the varwwwhtmlwebdir. Options Includes Exec. CGISave the file and restart Apache. Limiting Large Requests. By default Apache has no limit on the size of the HTTP request. This will allow an attacker to send a large amount of data. Apache has several directives that allow you to set a proper request size. This will protect your web server from a denial of service attack. You can set the value from 0 unlimited to 2. GB in the Apache main config file. For example, limit the request size of the varwwwhtmlwebdir. K. sudonanoetcapache. Addedit the following line Save the file and restart Apache. Disallow Browsing Outside the Document Root. It is recommended for Apache to be able to access only the document root directory. You can secure the root directory by setting the following line sudonanoetcapache. Addedit the following line Options None. Order deny,allow. Deny from all. This is what the code does Options None This will turn off all options. Order deny,allow The order in which the allow and deny commands are applied. Deny from all This will deny a request from all to the root directory. Save the file and restart Apache. Keep Apache Up to Date. New Apache updates will contain new fixes and patches that will reduce the vulnerability of your Apache server, so it is recommended to use the latest version of the Apache server. You can update your Apache to the latest version using the following command sudoapt get install apache. Conclusion. I hope this post will help you in securing your Apache server. You will find more advance security tips and tricks for securing the Apache server in my next post. Feel free to comment below if you have any questions.
4. WAFSQLModSecurity. In 2003, Nick Kew released a new module that complements Apaches modproxy and is essential for reverseproxying. Since then he gets regular questions and requests. A practical guide to secure and harden Apache Web Server. Introduction The Web Server is a crucial part of webbased applications. Apache Web Server is often. In this article we will discuss how to install, configure, and put them into play along with Apache on RHELCentOS 6 and 7 as well as Fedora 2115. In the screenshot above you can see the Apache version and the operating system installed in your server. This can be a major security issue for your web server. To hide this information, you need to edit Apaches main configuration file etcapache. Addedit the following line Server. Sql Server Update Date Part Of Date Time. Signature Off. Server. Tokens Prod. Save the file and restart apache service. Turn Off Directory Browsing and Disable Symbolic Links. By default directory listing is enabled in the Apache server. Directory listing displays all of the directory with all the files from the Apache server. If this is enabled, an attacker can easily view any file, analyse it and obtain sensitive information about an application. You can see the default directory listing in the image below. You can disable this setting by editing the Apache configuration file. Addedit the following line Options Follow. Sym. Links. Allow. Override None. Require all granted. Note the above code assumes that your web pages are served from the varwwwhtml folder. If you have changed the public folder to a custom location, change the Directory path in the above code. The line Options Follow. Serial Number Nanny Mania Arcade Town'>Serial Number Nanny Mania Arcade Town. Sym. Links also disables symbolic links. If you want to enable symbolic links, remove the sign in front of Follow. Sym. Links, so it becomes Options Follow. Sym. Links. Save the file and restart the Apache server. After this try to visit the Web in a browser, and you will get a forbidden error displayed in the below image. Disable Unnecessary Modules. By default Apache comes with several installed modules that are unnecessary for normal usage. It is recommended to trim the fat and disable all those unnecessary modules. You can list all enabled modules on your server using the following command sudolsetcapache. This will display the output as shown in the below image. From the above listed modules, some modules like status and autoindex are enabled but not needed. You can disable this modules using the following command sudo a. Make Use of Mod. Security. Mod security is a free Apache module used to protect your web server from various attacks like SQL injection, cross site scripting, session hijacking, brute force and a lot of other exploits. It also allows you to monitor traffic on a real time basis. You can install mod security using the following command sudoapt get install libapache. To check if the modsecurity module is running, use the following command sudoapachectl Mgrep color security. The image shown below indicates that the module was loaded. To enable the modsecurity rules, you need to rename and edit the mod security recommended configuration file and set the Sec. Rule. Engine option to On. For this run the following command sudomvetcmodsecuritymodsecurity. Addedit the following line Now restart Apache for the changes to take effect. There are lot of security rules that come with Modesecurity called the Core Rule Set that are located in the usrsharemodsecurity crs directory. Now you need to enable these rules to get it working with Apache. You can do this by editing the etcapache. Addedit the following line Include. Optional etcmodsecurity. Include. Optional usrsharemodsecurity crs Include. Optional usrsharemodsecurity crsbaserulesSave the file and restart Apache. Turn Off Server Side Includes and CGI Execution. It is recommended to disable server side includes and CGI execution if not needed. To do this you need to edit the Apache main config file. Addedit the following line Options Follow. Sym. Links Includes Exec. CGI. Allow. Override None. Require all granted. Save the file and restart Apache. You can also do this for a specific directory. For example, to turn off server side includes and cgi file executions for the varwwwhtmlwebdir. Options Includes Exec. CGISave the file and restart Apache. Limiting Large Requests. By default Apache has no limit on the size of the HTTP request. This will allow an attacker to send a large amount of data. Apache has several directives that allow you to set a proper request size. This will protect your web server from a denial of service attack. You can set the value from 0 unlimited to 2. GB in the Apache main config file. For example, limit the request size of the varwwwhtmlwebdir. K. sudonanoetcapache. Addedit the following line Save the file and restart Apache. Disallow Browsing Outside the Document Root. It is recommended for Apache to be able to access only the document root directory. You can secure the root directory by setting the following line sudonanoetcapache. Addedit the following line Options None. Order deny,allow. Deny from all. This is what the code does Options None This will turn off all options. Order deny,allow The order in which the allow and deny commands are applied. Deny from all This will deny a request from all to the root directory. Save the file and restart Apache. Keep Apache Up to Date. New Apache updates will contain new fixes and patches that will reduce the vulnerability of your Apache server, so it is recommended to use the latest version of the Apache server. You can update your Apache to the latest version using the following command sudoapt get install apache. Conclusion. I hope this post will help you in securing your Apache server. You will find more advance security tips and tricks for securing the Apache server in my next post. Feel free to comment below if you have any questions.